Azure Pipelines: How to add a build agent with Azure Container Instances
Context
Had enough waiting for a build agent to be available?
Have some Parallel jobs available and looking for a way to exploit them ponctually?
Let’s see how to run a container on Azure Container Instances to get a ponctual extra build agent available in few minutes for your Azure DevOps project.
Reuse microsoft container images with tools already installed
The simplest way to get an Azure DevOps build agent running in 1 command line is to reuse one of Microsoft container image available.
The command line to start a build agent on Azure Container Instances should look like the following:
az container create -g MY_RESOURCE_GROUP -n MY_CONTAINER_NAME --image mcr.microsoft.com/azure-pipelines/vsts-agent --cpu 1 --memory 7 --environment-variables VSTS_ACCOUNT=MY_ACCOUNT_NAME VSTS_TOKEN=MY_VSTS_TOKEN VSTS_AGENT=MY_AGENT_NAME VSTS_POOL=Default
Where :
--imagecorresponds to one of the image from the page Azure Pipelines AgentVSTS_ACCOUNTcorresponds to your Azure DevOps account nameVSTS_TOKENcorresponds to a PAT (Personal Access Token), used to access to your Azure DevOps account. To generate one follow Create personal access tokens to authenticate accessVSTS_AGENTcorresponds to your build agent name, displayed in Azure DevOpsVSTS_POOLcorresponds to the agent pool where you want your build agent to belong to. Default to theDefaultagent pool.
You can find more information of other parameters used in az container create command line on docs.microsoft.com
Example
az container create -g aci-vfa-rg -n my-aci-agent --image mcr.microsoft.com/azure-pipelines/vsts-agent --cpu 1 --memory 7 --environment-variables VSTS_ACCOUNT=vivien VSTS_TOKEN=5a7jwwhoj64nlcyxcxahnj2v74zifcijg6xzcpkun6kdutjlk2sq VSTS_AGENT=my-aci-agent VSTS_POOL=Default
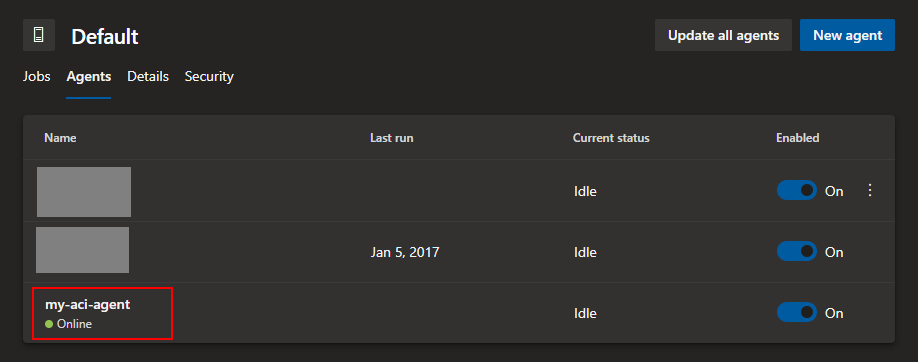
Et voilà! Your new agent is ready to run your Azure Pipelines!
Pricing
Ok great, you have now your agent, but how much does it cost you per execution ?
Let’s do some math: We have 7 GB of memory, during let’s say 20 minutes. If we check the pricing page of ACI, the price of 1 second for 1 GB is $0.0000015, which gives us: 7 * 20 * 60 * 0.0000015 = 0.01176$
Let’s do the same with the CPU usage. For 1 core during 20 minutes with a price of 0.0000130$ per second, that gives us: 20 * 60 * 0.0000130 = 0.0156$
Which gives us a total of 0.02736$ (around 3 cents) per 20 minutes of execution !
So in summary, we get a build execution on ACI for around 3 cents :)
To go further
When need, you just need to run the the az container stop to stop the container (and stop paying for it), as well as az container start to make it available again!
However the main drawback of the already existing Microsoft images is that they take around 10 minutes to be pulled off (and start) as the image size if more than 10GB. Depending on your context, this could be a real blocker, and one of the best way to answer to this problem is by creating your own “custom” image, which will bring only your needed dependencies (*and not the tooling for all languages available in the world *:)) and enable you to get your agent in seconds!
But this will be the subject of an another blog post :)
May the code be with you!
Bonus - Get Containers logs in Azure Log Analytics (Azure Monitor)
Your containers logs are directlly available from the Azure Portal:
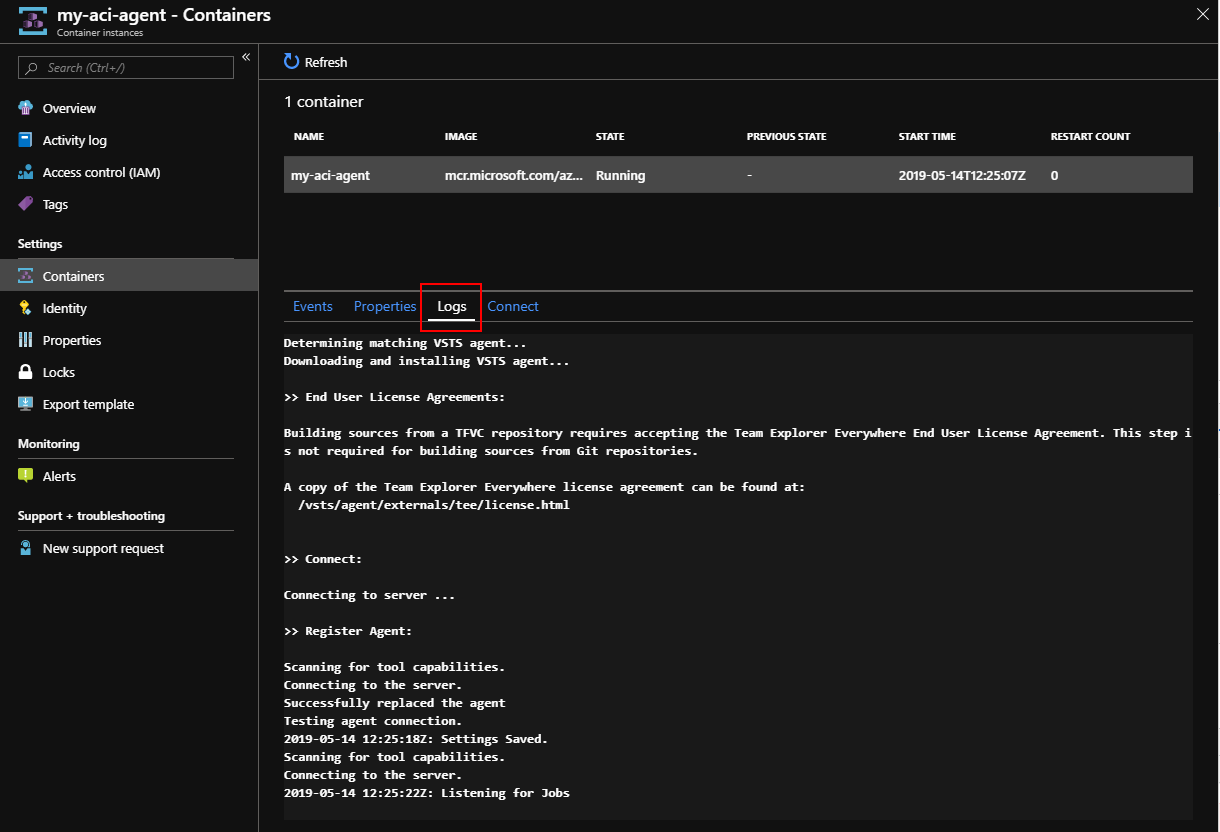
If you want to store your container logs, you can send them to an Azure Log Analytics workspace by specifying few more parameters to the az container create command line.
As a prerequisite, you need to have an Azure Log Analytics workspace available (Check this section from my previous blog post to create one), and retrieve your WORKSPACE ID and PRIMARY KEY.
Then add to your az container create command the parameters:
--log-analytics-workspacecorresponding to yourWORKSPACE ID--log-analytics-workspace-keycorresponding to yourPRIMARY KEY
Enjoy browsing your logs through Azure Log Analytics!